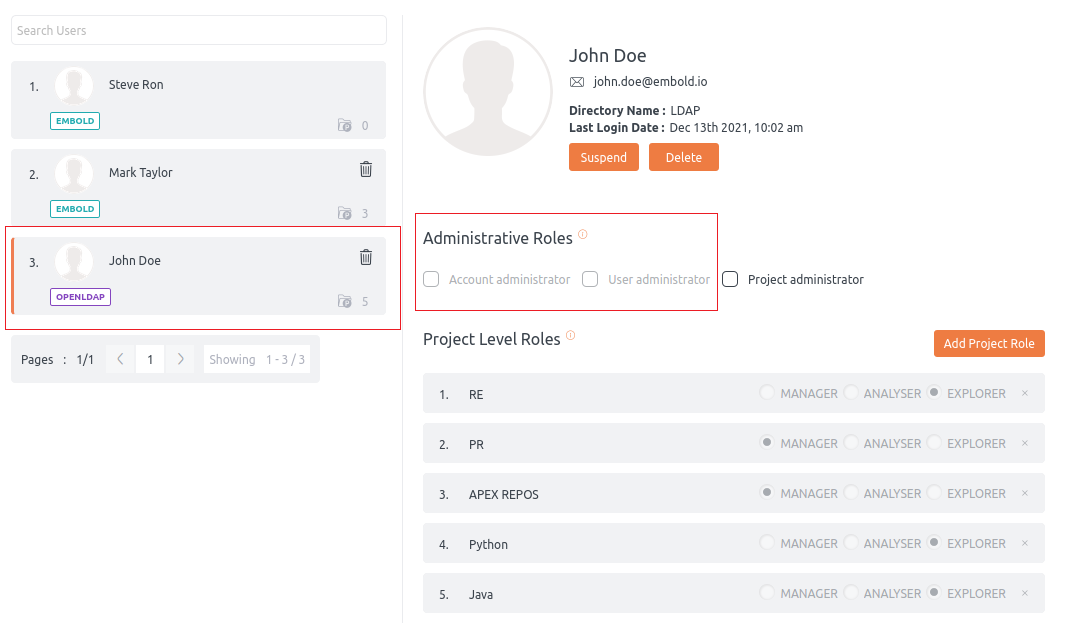
LDAP (Lightweight Directory Access Protocol) is used for directory service authentication and automatically maps with the roles.
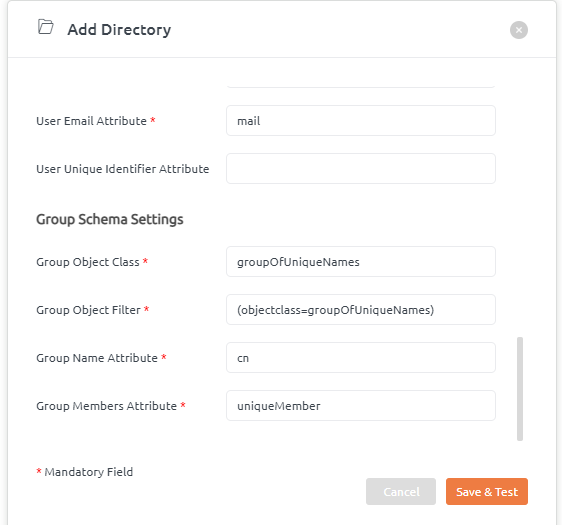
How to configure group schema settings?
Multiple users are associated in a group.
- Navigate to the User Directories tab in the administration section.
- Click on Add Directory button to open Add Directory popup.
- Go to Group Schema Settings. Add details.
Global role:
Predefined groups from LDAP are mapped to BrowserStack Code Quality global roles. These roles are:
- code_quality_account_admin– This role maps to Account administrator in BrowserStack Code Quality UI.
- code_quality_project_admin– This role maps to the Project administrator in BrowserStack Code Quality UI.
- code_quality_user_admin– This role maps to User administrator in BrowserStack Code Quality UI.
Read more about the administrative roles here.
Project level role:
Predefined groups from LDAP are mapped to BrowserStack Code Quality project level roles. These roles are:
- code_quality_manager_{project_name}: This role maps to BrowserStack Code Quality’s manager role and its associated project name.
E.g. code_quality_manager_PROJECTA - code_quality_analyser_{project_name}: This role maps to BrowserStack Code Quality’s analyzer role and its associated project name.
E.g. code_quality_analyser_PROJECTA - code_quality_explorer_{project_name}: This role maps to BrowserStack Code Quality’s explorer role and its associated project name.
E.g. code_quality_explorer_PROJECTA - code_quality_contributor_{project_name}: This role maps to BrowserStack Code Quality’s contributor role and its associated project name.
E.g.,code_quality_contributor_PROJECTA
Read more about the project level roles here.
- If any project name gets defined in the LDAP group, BrowserStack Code Quality cannot assign that project to the user. The role will be disabled from Administrative role or Project Level role.
For example, Project RE is in LDAP; this will be disabled from BrowserStack Code Quality UI (i.e., From Project level roles).