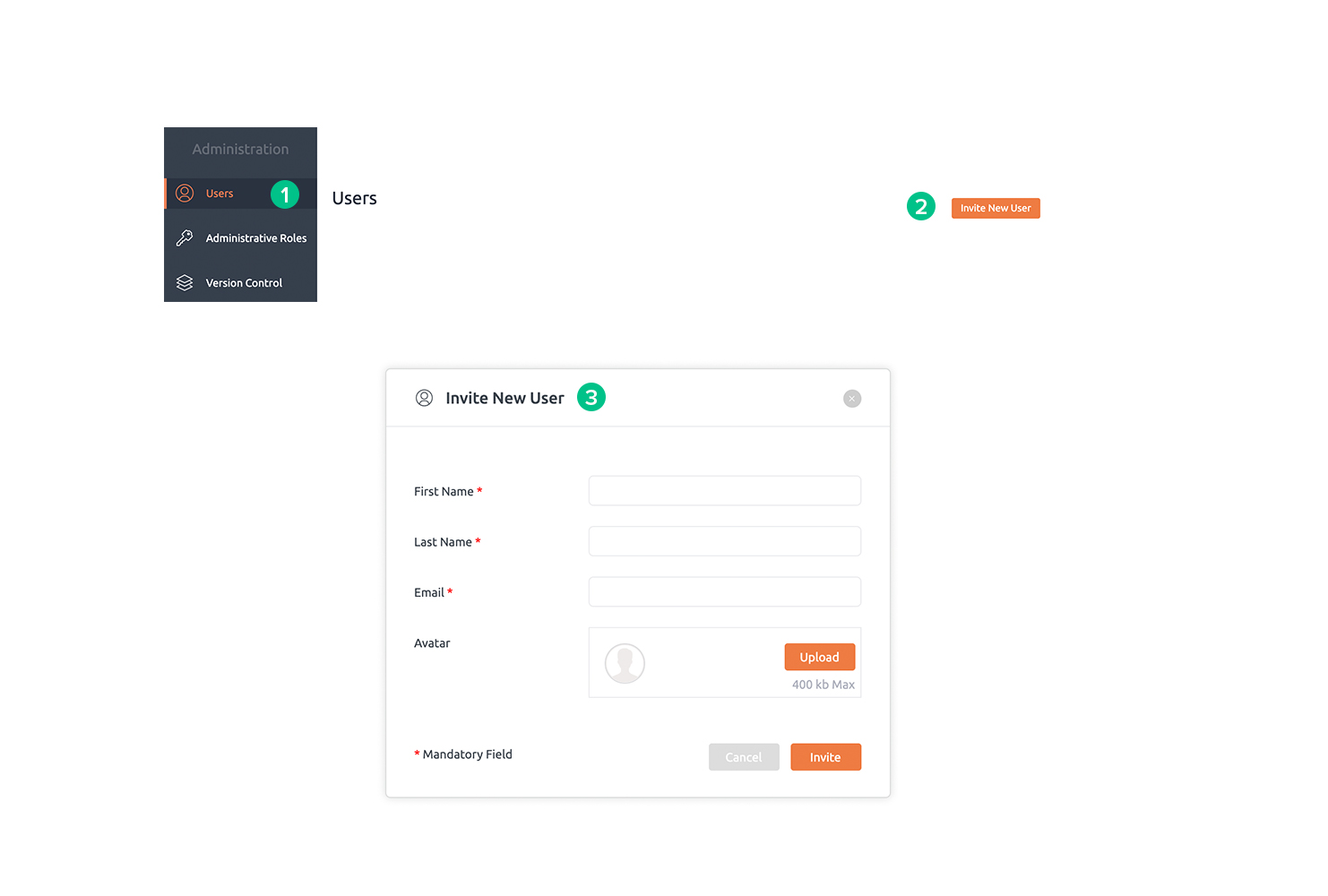
Invite new user
- Navigate to users tab in administration section.
- Click on the Invite New User button.
- Fill the user details and click Invite button.
- User will get an invitation to join BrowserStack Code Quality and will get added to the list of users.
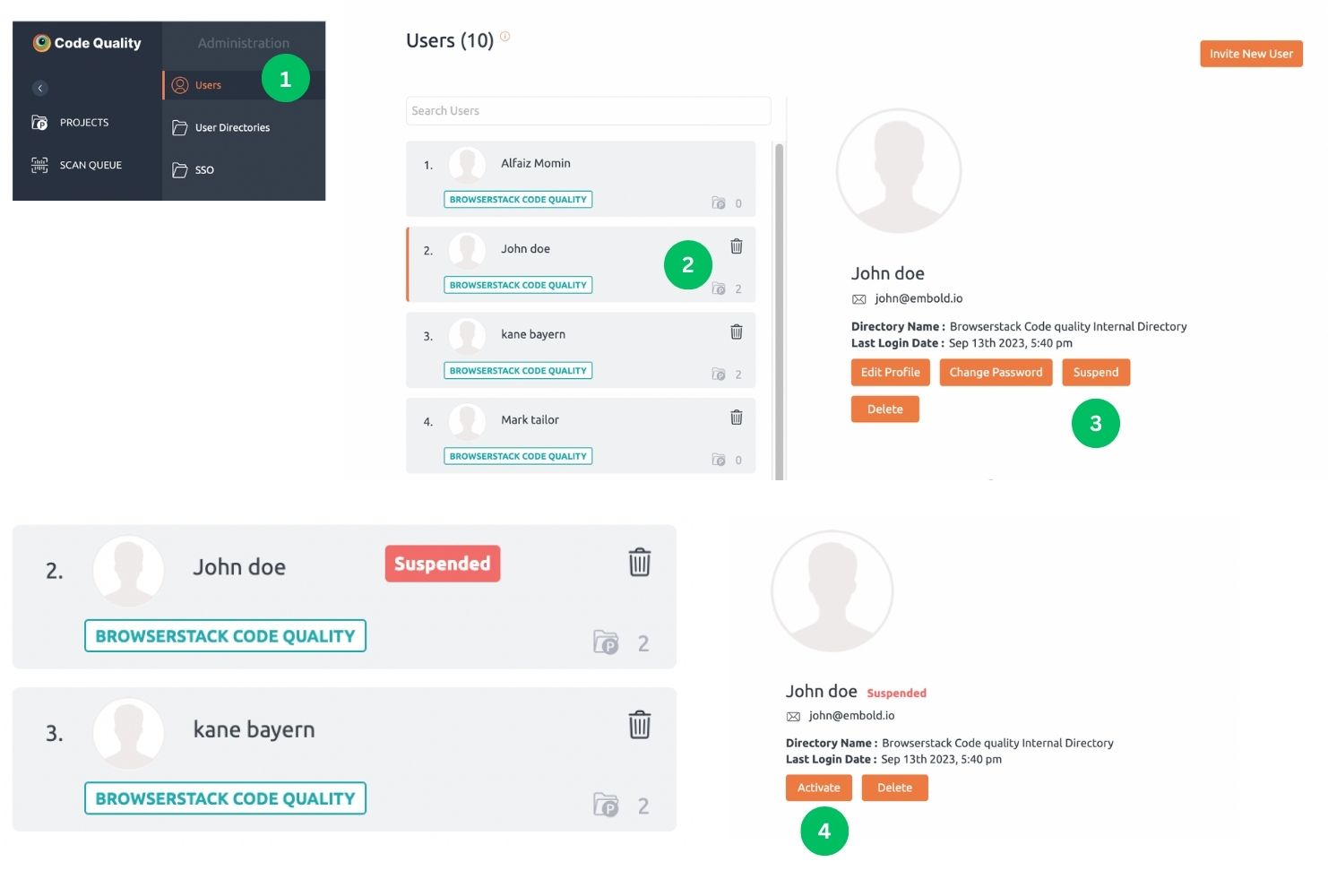
Suspend a user
Steps for suspending a user:
1. Navigate to the Users tab in the administration section.
2. Choose the user to be suspended.
3. Click the Suspend button. The user status will be changed to Suspended.
Note: A suspended user will retain all of their settings and information while removing their access. Suspended users do not count towards your licensed seats.
4. The administrator can reactivate the suspended user by clicking on the Activate button.
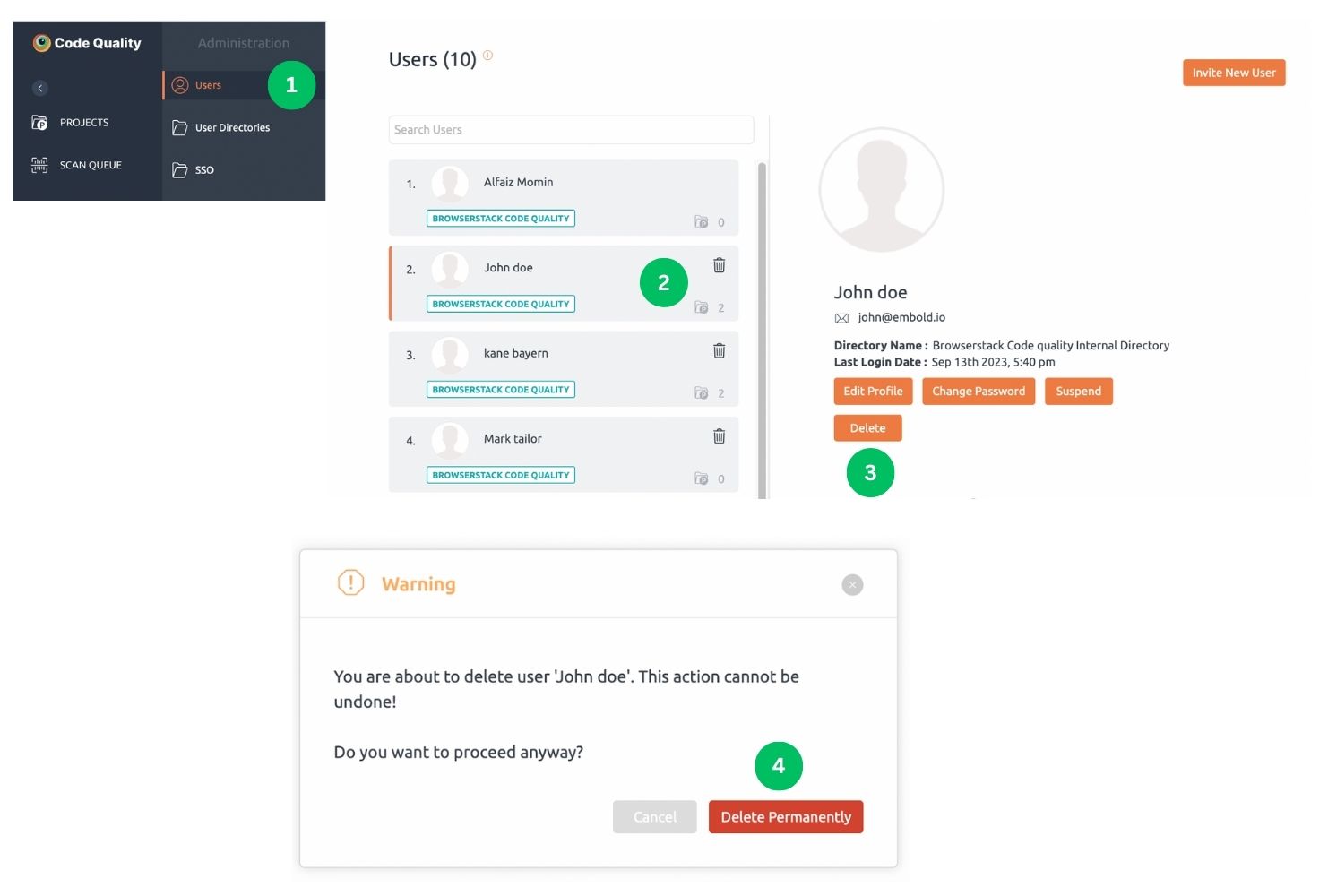
Delete a user
Steps for deleting a user:
1. Navigate to the Users tab in the administration section.
2. Choose the user to be deleted.
3. Click the Delete button.
4. A warning pop-up is displayed to ensure the action, click Delete Permanently to remove the user.
Different User Roles and Permissions
Account Administrator
- Description: The highest privilege role, granting complete administrative access across all levels of BrowserStack Code Quality. Account administrators manage projects, repositories, users, and system-wide settings.
- Permissions:
- Project Level: Create, edit, delete projects, and manage users.
- Repository Level: Full access, including scan operations, repository linking/unlinking, and configuration settings.
- User Level: Invite, edit, suspend, and delete users.
- Administrative Settings: Access SSO, user directories, licenses, quality gate profiles, and notifications.
- Left Menu Options: Access to all system settings and controls.
Project Administrator
- Description: Focused on project-level management, including creating, editing, and deleting projects and managing project repositories.
- Permissions:
- Project Level: Create, edit, delete projects, and manage associated repositories.
- Repository Level: Full access to repository operations within the assigned project.
- User Level: No access to user management.
- Administrative Settings: Limited to managing quality gate profiles and notifications within assigned projects.
- Left Menu Options: Access project-specific settings, repositories, and quality gate profiles.
User Administrator
- Description: Specializes in user management, with no access to projects or repositories.
- Permissions:
- Project Level: No permissions.
- Repository Level: No permissions.
- User Level: Full access to invite, edit, suspend, and delete users.
- Administrative Settings: Focused on user-related administrative tasks.
- Left Menu Options: Access user management settings.
Manager
- Description: Oversees project and repository management tasks, with the ability to perform scans and manage configurations.
- Permissions:
- Project Level: Edit projects, manage users, and enable project creation (with
allow_manage_projectpermission). - Repository Level: Perform scans, configure repositories, link/unlink repositories, and manage quality gates and issue tracker integrations.
- User Level: No access.
- Administrative Settings: Limited to project-level settings like notifications and repository management.
- Left Menu Options: Access repository and project-specific settings.
- Project Level: Edit projects, manage users, and enable project creation (with
Analyser
- Description: Focuses on code quality analysis tasks, including scanning repositories and configuring repository settings.
- Permissions:
- Project Level: No project management permissions.
- Repository Level: Perform scans, view scan history, configure repositories, and manage snapshots.
- User Level: No access.
- Administrative Settings: Limited to repository-specific tasks.
- Left Menu Options: View and access repository-related information.
Explorer
- Description: A read-only role primarily for viewing scan results, repository details, and dashboards.
- Permissions:
- Project Level: No permissions for creation, editing, or deletion.
- Repository Level: View scan history and repository details.
- User Level: No access.
- Administrative Settings: Limited to viewing notifications.
- Left Menu Options: Restricted to viewing relevant details.
Contributor
- Description: A specific role focusing on contributing to assigned projects by managing snapshots and performing scans.
- Permissions:
- Project Level: Similar to explorer with added responsibilities like managing snapshots.
- Repository Level: Access to perform scans, view history, and manage snapshots.
- User Level: No access.
- Administrative Settings: Limited to notifications and repository configurations.
- Left Menu Options: Access relevant repository and project-specific settings.
Refer to the tables below to check permissions for different user levels and roles.
Here is the table format representation for each set of permissions:
Project Level Permissions :
| ype | Account Administrator | Project Administrator | User Administrator | Manager | Analyser | Explorer | Contributor |
|---|---|---|---|---|---|---|---|
| Project Create | Yes | Yes | No | No / (Yes with allow_manage_project) | No / (Yes with allow_manage_project) | No / (Yes with allow_manage_project) | No |
| Project Edit | Yes | Yes | No | Yes | No | No | No |
| Project Delete | Yes | Yes | No | Yes | No | No | No |
| Manage Users | Yes | Yes | No | Yes | No | No | No |
Repository Level Permissions :
| Type | Account Administrator | Project Administrator | User Administrator | Manager | Analyser | Explorer | Contributor |
|---|---|---|---|---|---|---|---|
| Scan Repository | Yes | Yes | No | Yes | Yes | No | Yes |
| Scan History | Yes | Yes | No | Yes | Yes | Yes | Yes |
| Snapshots Pin | Yes | Yes | No | Yes | Yes | No | No |
| Scan Configuration | Yes | Yes | No | Yes | Yes | No | No |
| Code Checkers Configuration | Yes | Yes | No | Yes | Yes | No | No |
| Download Repository Configuration | Yes | Yes | No | Yes | Yes | No | Yes |
| Disable/Enable Suppression Approval | Yes | Yes | No | Yes | No | No | No |
| Quality Gate Profile | Yes | Yes | No | No | No | No | No |
| Issue Tracker Integration | Yes | Yes | No | Yes | No | No | No |
| Link/Unlink a Repository | Yes | Yes | No | Yes | No | No | No |
| Delete Repository Permanently | Yes | Yes | No | Yes | No | No | No |
| Edit Repository | Yes | Yes | No | Yes | No | No | No |
User Level Permissions :
| Type | Account Administrator | Project Administrator | User Administrator | Manager | Analyser | Explorer | Contributor |
|---|---|---|---|---|---|---|---|
| Invite New User | Yes | No | Yes | No | No | No | No |
| Edit Profile | Yes | No | Yes | No | No | No | No |
| Change Password | Yes | No | Yes | No | No | No | No |
| Suspend User | Yes | No | Yes | No | No | No | No |
| Delete User | Yes | No | Yes | No | No | No | No |
| Administrative Roles | Yes | No | No | No | No | No | No |
| Project Level Roles | Yes | No | No | No | No | No | No |
Left Menu Options :
| Option | Account Administrator | Project Administrator | User Administrator | Manager | Analyser | Explorer | Contributor |
|---|---|---|---|---|---|---|---|
| Users | Yes | No | Yes | No | No | No | No |
| User Directories | Yes (if directoryEnabled) | No | No | No | No | No | No |
| SSO | Yes (if ssoEnabled) | No | No | No | No | No | No |
| Administrative Roles | Yes | No | No | No | No | No | No |
| Version Control | Yes | Yes | No | No | No | No | No |
| Repositories | Yes | Yes | No | No | No | No | No |
| KPIs | Yes | No | No | No | No | No | No |
| Tags | Yes | No | No | No | No | No | No |
| Groups | Yes (if enableGroup) | Yes | No | No | No | No | No |
| Quality Gate Profile | Yes | Yes | No | No | No | No | No |
| Access Token | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Backup and Purge | Yes (if is_cloud) | No | No | No | No | No | No |
| License | Yes | No | No | No | No | No | No |
| URL Forwarding | Yes (if enableCommitScan & is_cloud) | No | No | No | No | No | No |
| Notifications | Yes | Yes | Yes | Yes | Yes | Yes | No |
| RE Setting | Yes (if enableREScan) | Yes | No | No | No | No | No |
