Directory Service Integration
You can now use BrowserStack Code Quality to integrate LDAP directory services. To do that, you need to just Add Directory, Test Directory and Login to BrowserStack Code Quality. At the moment, we support OpenLDAP and Microsoft Active Directory services only. We will be adding support to more directory services later on.
Steps to add directory:
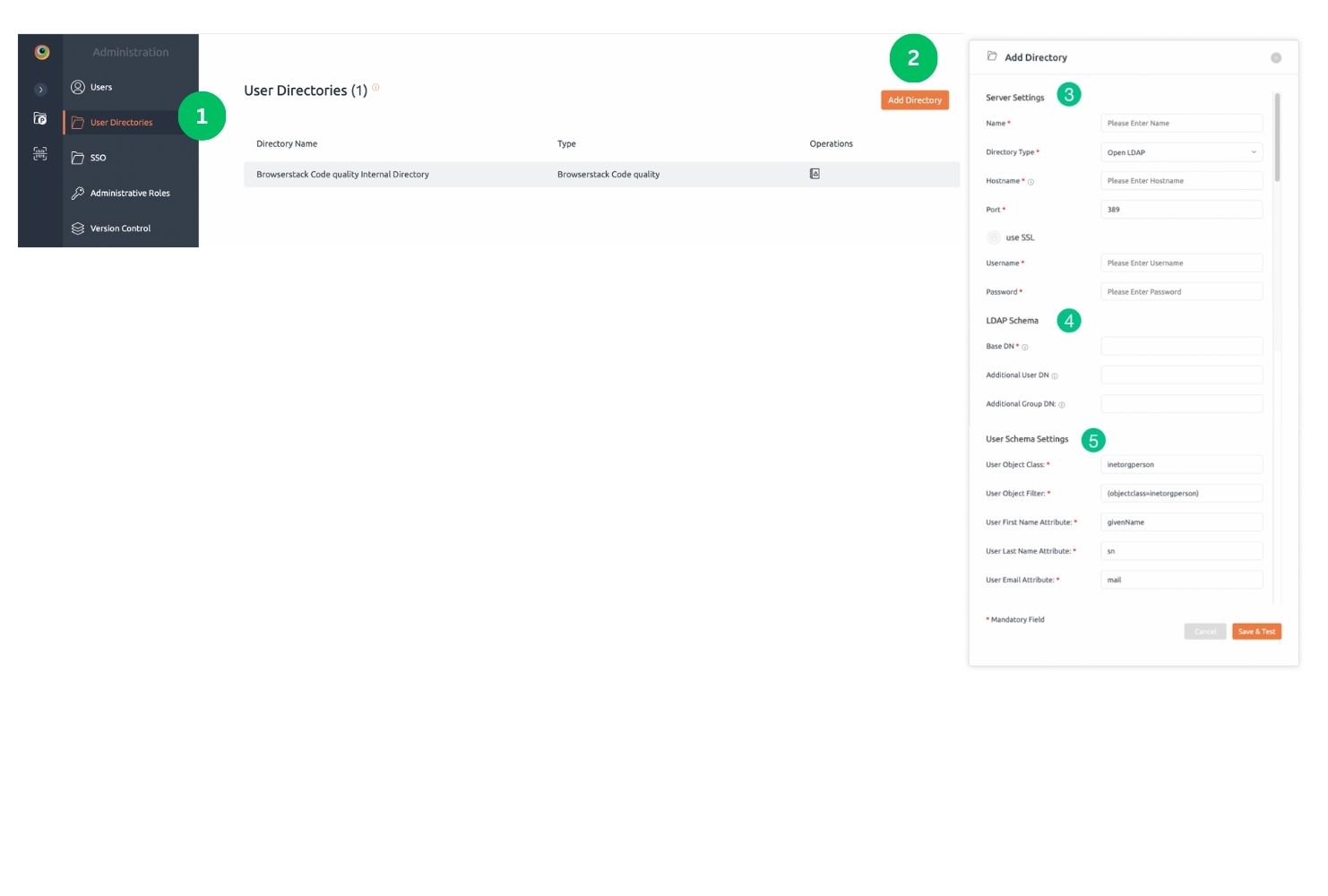
- Navigate to the User Directories tab in the administration section.
- Click on Add Directory button to open Add Directory popup.
- Enter directory Server Settings form field details.
- Enter directory LDAP Schema details.
- Enter directory User Schema Settings details.
- After filling all the form fields, click Save & Test button. Know more about directory fields.
- Users will get a notification message and will get added to the list of directories.
Steps to test directory:
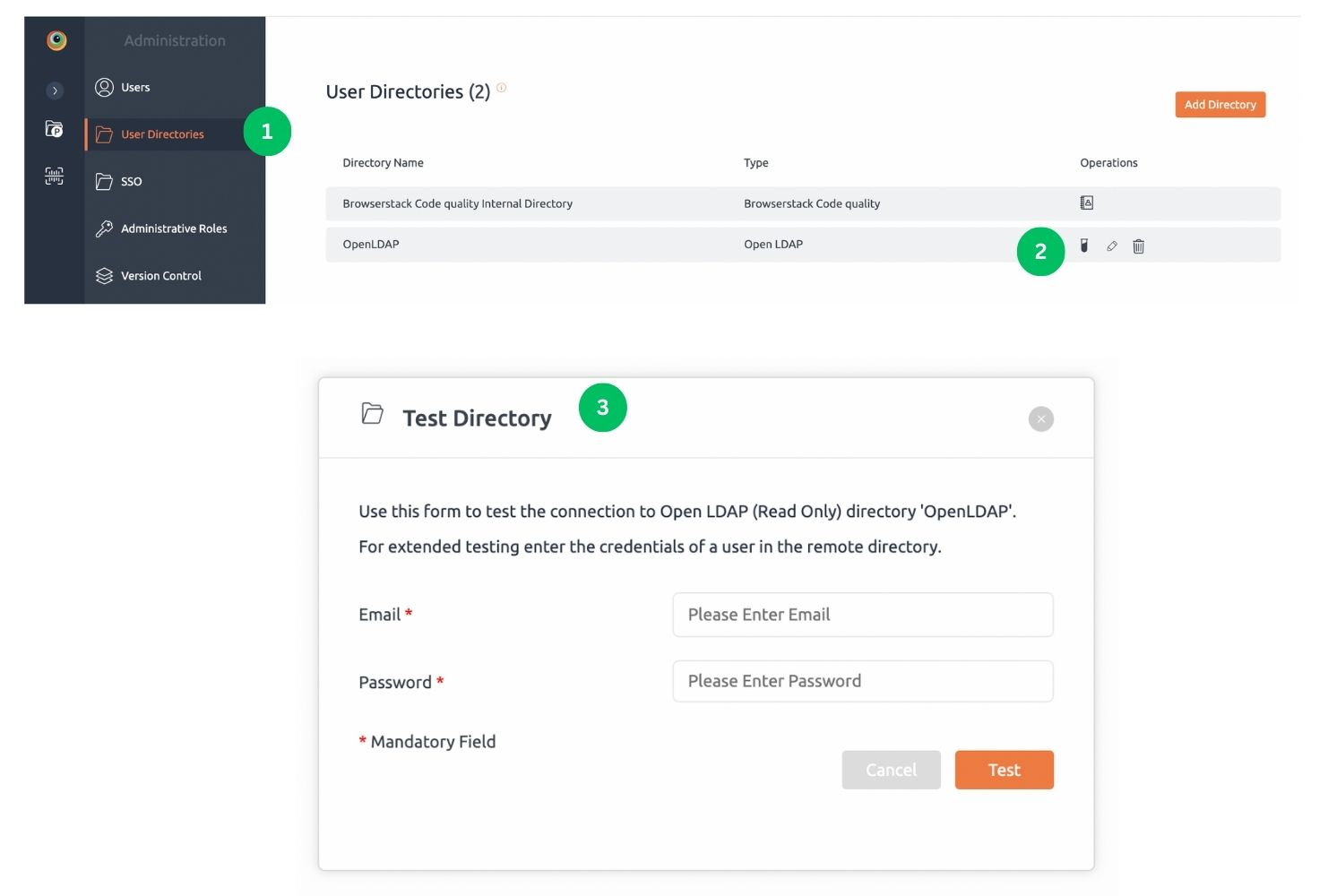
- Navigate to User Directories tab in administration section.
- You will see list of all directories and besides each external directory you will see Test icon.
- Click on Test icon to open Test Directory popup.
- Enter valid LDAP user credentials and click Test button.
- User will get a notification message about Test Directory.
- If successful then you are ready to Login to BrowserStack Code Quality.
- In case of failure, you will see Invalid Credentials message there. Try again, using valid LDAP user credentials.
Steps to remove directory:
- Navigate to User Directories tab in administration section.
- You will see list of all directories and besides each external directory you will see three icons such as Test, Edit and Remove.
- Click on the Remove icon which will open Warning popup.
- Click on Delete Permanently button to remove directory permanently from BrowserStack Code Quality.
LDAP configuration
LDAP (Lightweight Directory Access Protocol) is used for directory service authentication and automatically maps with the roles.
How to configure group schema settings?
Multiple users are associated in a group.
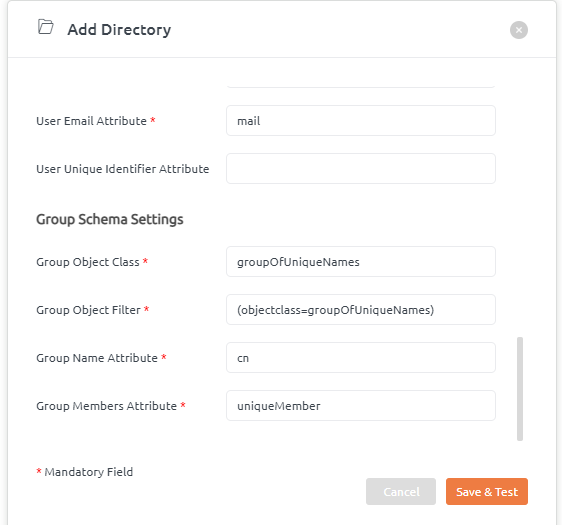
- Navigate to the User Directories tab in the administration section.
- Click on Add Directory button to open Add Directory popup.
- Go to Group Schema Settings. Add details.
Global role:
Predefined groups from LDAP are mapped to BrowserStack Code Quality global roles. These roles are:
- code_quality_account_admin– This role maps to Account administrator in BrowserStack Code Quality UI.
- code_quality_project_admin– This role maps to the Project administrator in BrowserStack Code Quality UI.
- code_quality_user_admin– This role maps to User administrator in BrowserStack Code Quality UI.
Read more about the administrative roles here.
Project level role:
Predefined groups from LDAP are mapped to BrowserStack Code Quality project level roles. These roles are:
- code_quality_manager_{project_name}: This role maps to BrowserStack Code Quality’s manager role and its associated project name.
E.g. code_quality_manager_PROJECTA - code_quality_analyser_{project_name}: This role maps to BrowserStack Code Quality’s analyzer role and its associated project name.
E.g. code_quality_analyser_PROJECTA - code_quality_explorer_{project_name}: This role maps to BrowserStack Code Quality’s explorer role and its associated project name.
E.g. code_quality_explorer_PROJECTA - code_quality_contributor_{project_name}: This role maps to BrowserStack Code Quality’s contributor role and its associated project name.
E.g.,code_quality_contributor_PROJECTA
Read more about the project level roles here.
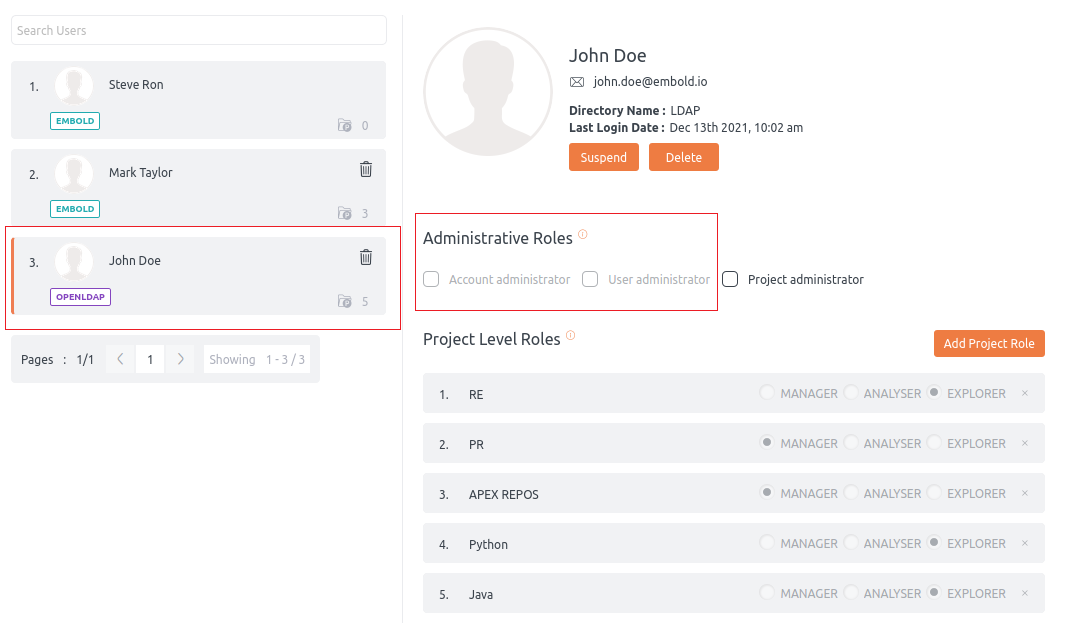
- If any project name gets defined in the LDAP group, BrowserStack Code Quality cannot assign that project to the user. The role will be disabled from Administrative role or Project Level role.
For example, Project RE is in LDAP; this will be disabled from BrowserStack Code Quality UI (i.e., From Project level roles).
About Directory Fields
Server Settings
- Name: Enter a meaningful name to help you identify the LDAP directory server.
Example: My Enterprise Directory, Corporate LDAP Directory etc. - Directory Type: Select the type of LDAP directory that you will connect to. If you are adding a new LDAP connection, the value you select here will determine the default values for many of the options on the rest of screen.
Example: Microsoft Active Directory, OpenLDAP etc. - Hostname: The host name of your directory server.
Example: ad.example.com, ldap.example.com etc. - Port: The port on which your directory server is listening.
Example: 389, 10389, 636 (in case, SSL enabled) etc. - Use SSL: Check this if the connection to the directory server is an SSL (Secure Sockets Layer) connection. Note that you will need to configure an SSL certificate in order to use this setting.
- Username: The distinguished name of the user that the application will use when connecting to the directory server.
Example: cn=admin,dc=ldap,dc=example,dc=com - Password: The password of the user specified above.
Note: Connecting to an LDAP server requires that this application log in to the server with the username and password configured here. As a result, this password cannot be one-way hashed – it must be recoverable in the context of this application. The password is currently stored in the database in encrypted format. To guarantee its security, you need to ensure that other processes do not have OS-level read permissions for this application’s database or configuration files.
LDAP schema
- Base DN: The root distinguished name (DN) to use when running queries against the directory server.
Example: cn=users,dc=ldap,dc=example,dc=com
For Microsoft Active Directory, specify the base DN in the following format: dc=ad,dc=example,dc=com. You will need to replace the ad, example and com with your specific domain component configuration. - Additional User DN: This value is used in addition to the base DN when searching and loading users. If no value is supplied, the sub-tree search will start from the base DN.
Example: ou=Users - Additional Group DN: This value is used in addition to the base DN when searching and loading groups. If no value is supplied, the sub-tree search will start from the base DN.
Example: ou=Groups
User schema settings
- User Object Class: This is the name of the class used for the LDAP user object.
Example: user, person, inetOrgPerson etc. - User Object Filter: The filter to use when searching user objects.
Example openLDAP: (&(objectClass=person)(|(ou:dn:=RND)(ou:dn:=HR)))
Example MS AD: (&(objectCategory=Person)(sAMAccountName=*)) - User First Name Attribute: The attribute field to use when loading the user’s first name.
Example: givenName - User Last Name Attribute: The attribute field to use when loading the user’s last name.
Example: sn - User Email Attribute: The attribute field to use when loading the user’s email address. This attribute is used for login into BrowserStack Code Quality.
Example: mail
