SSO
BrowserStack Code Quality currently supports SAML. Only authentication is allowed with SAML SSO.
SAML
SAML (Security Assertion Markup Language) is mainly used for authentication purposes.
Tested on : Okta , Auth0 , Azure SAML and OneLogin
How to go to SSO Settings?
Navigate to the SSO tab in the administration section. SSO Settings page will be displayed that contains a list of providers.
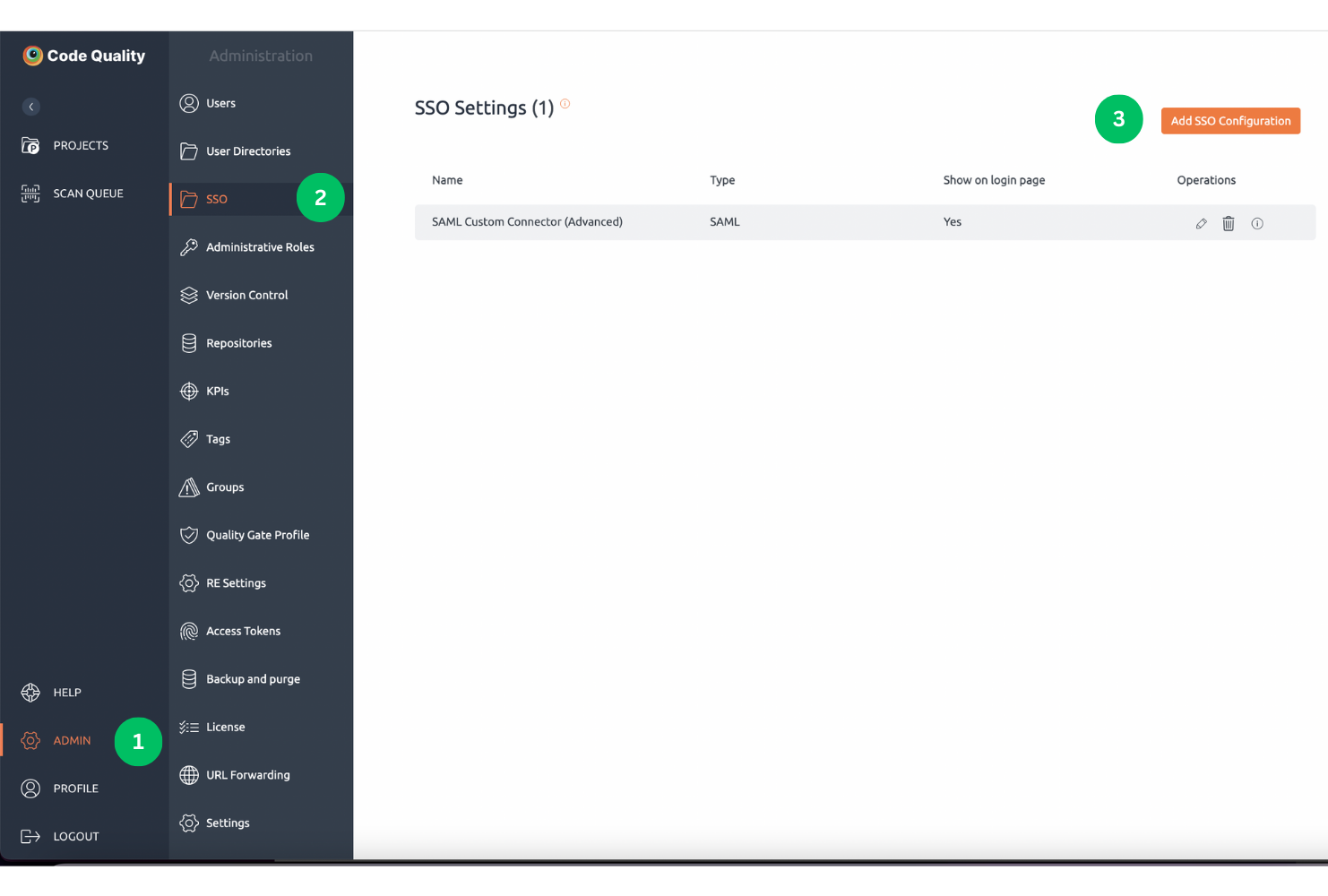
Currently, this SSO is only available for on-premise customers and not on the cloud.
Configuration Settings
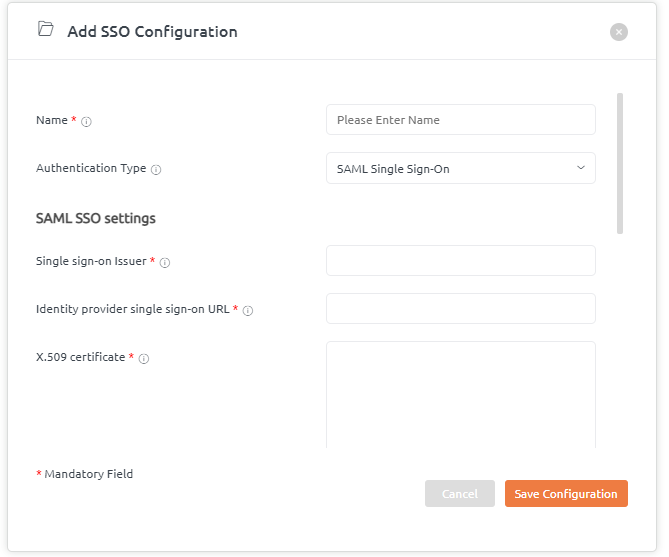
Click on Add SSO Configuration button. A below pop-up window will be displayed. It has the following fields:
- Enter the name for SSO configuration.
- By default SAML Single Sign-on Authentication type is displayed.
- Add details about SAML SSO settings like entity ID, SAML SSO 2.0 URL, X.509 certificate from your provider.
Attribute mapping here states that IDP attributes are mapped with the BrowserStack Code Quality user’s data according to SAML’s response.
Add details for the Attributes mapping like email id, first name, and last name.
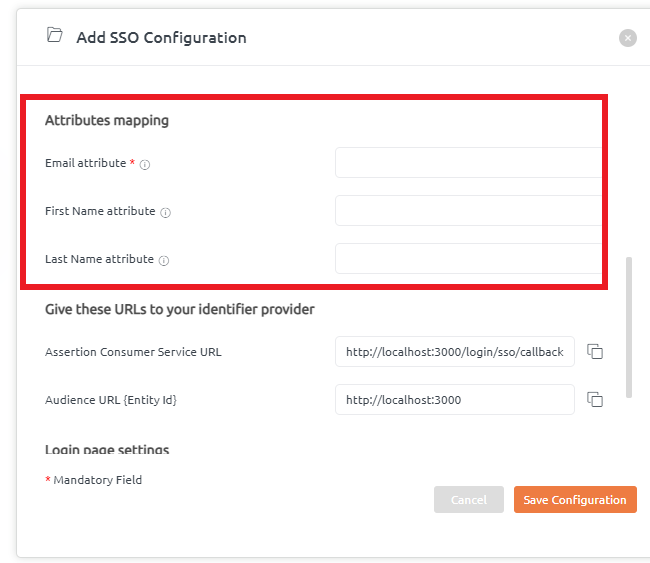
BrowserStack Code Quality provides Assertion Customer Service URL and Audience URL that needs to be given to the identifier provider. So, these URLs will be configured at the provider’s side.
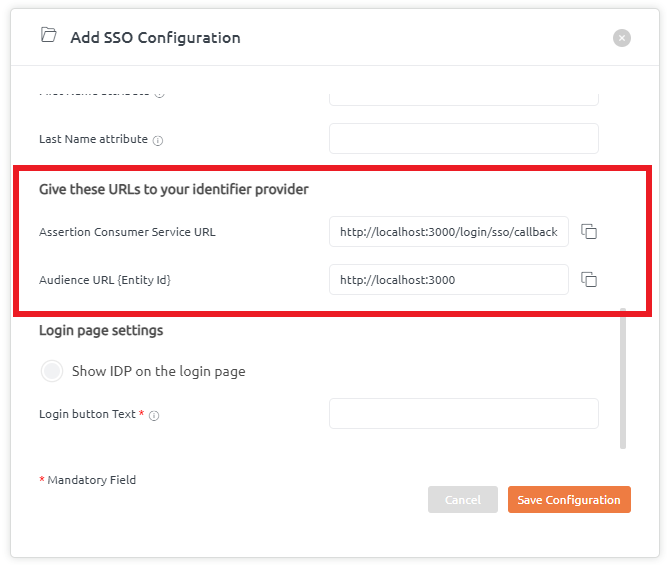
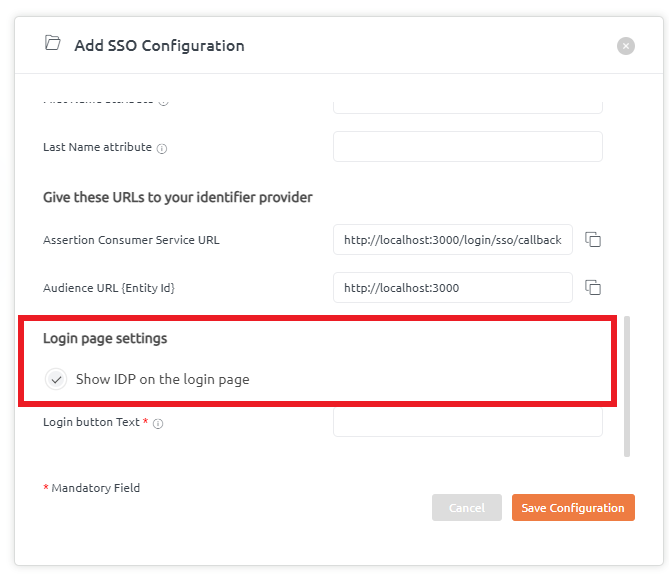
Login Page settings help to showcase the IDP name on the login page.
Users can tick this checkbox to enable the IDP name to be displayed on the login page. By default, this is enabled.
If the tickbox is unchecked, this feature will be disabled.
Moreover, there is a provision to add Login text button details as per your choice.
Once, when all the above details are filled in, click on the “Save Configuration” button.
SSO Configuration details added successfully.
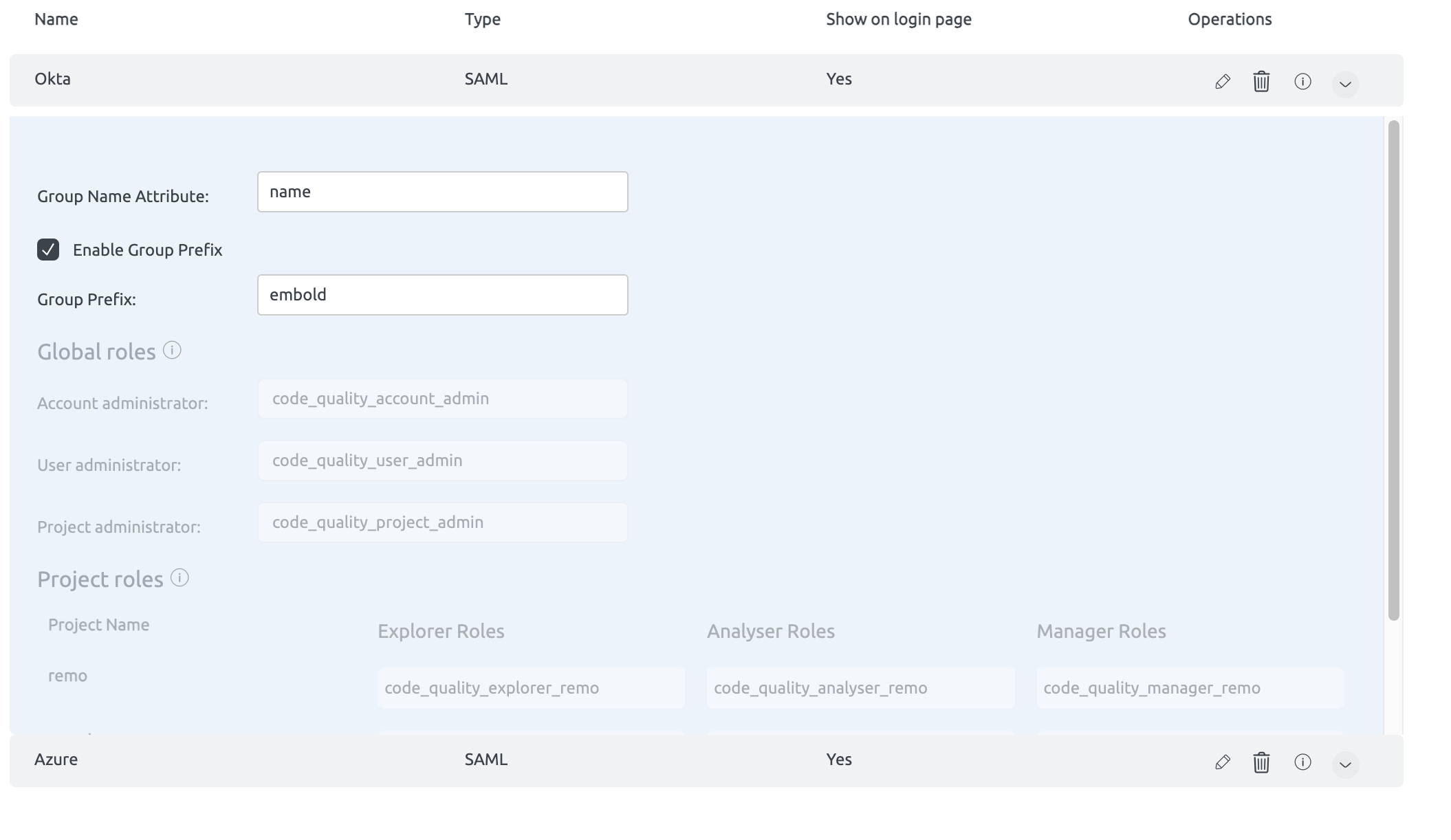
Group Mapping
This document provides detailed information on how predefined groups from SSO are mapped to global and project-level roles in BrowserStack Code Quality. This mapping facilitates role-based access control within BrowserStack Code Quality through Single Sign-On (SSO) integration.
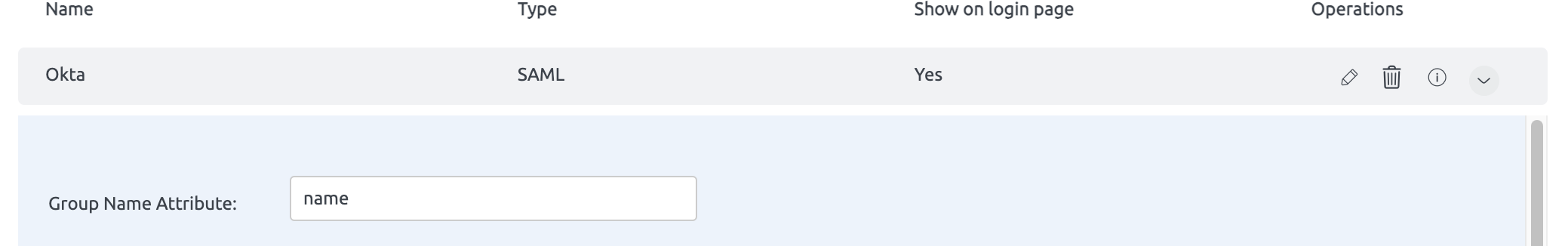
Providing Group Name Attribute
To successfully map groups, you must provide the group name attribute. This attribute is used to identify and map the appropriate SSO group to its corresponding role in BrowserStack Code Quality.
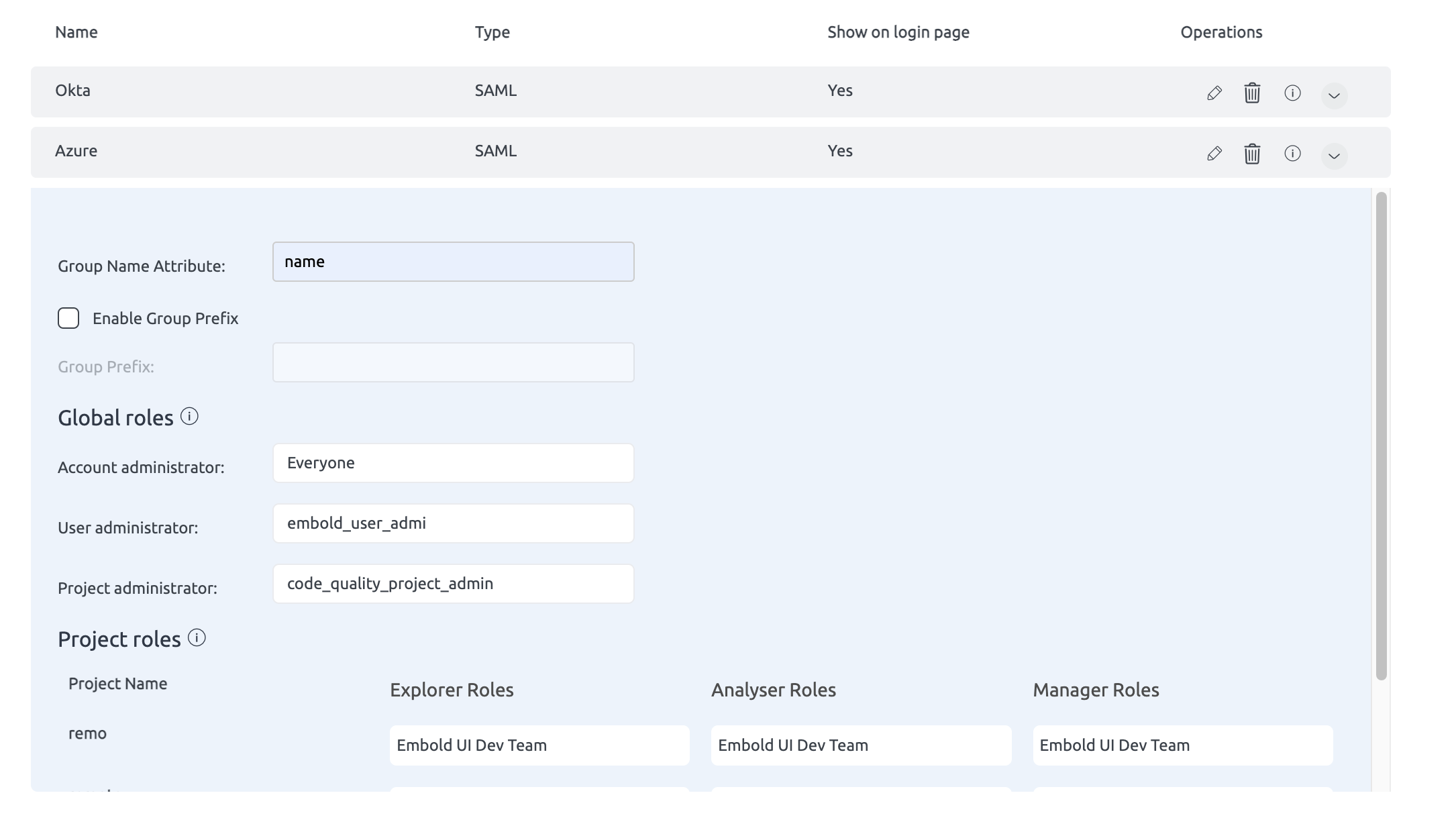
Global Roles Mapping
Predefined SSO Groups and Corresponding Global Roles
- code_quality_account_admin
- BrowserStack Role: Account Administrator
- Description: Users with this role have administrative access to the entire BrowserStack Code Quality account.
- code_quality_project_admin
- BrowserStack Role: Project Administrator
- Description: Users with this role can administer specific projects within the BrowserStack Code Quality environment.
- code_quality_user_admin
- BrowserStack Role: User Administrator
- Description: Users with this role can manage user access and permissions within BrowserStack Code Quality.
Project-Level Roles Mapping
Predefined SSO Groups and Corresponding Project-Level Roles
- code_quality_manager_{project_name}
- BrowserStack Role: Project Manager
- Description: Users with this role can manage all aspects of the specified project.
- Example:
code_quality_manager_PROJECTA
- code_quality_analyser_{project_name}
- BrowserStack Role: Project Analyzer
- Description: Users with this role can scan , analyze and review code quality within the specified project.
- Example:
code_quality_analyser_PROJECTA
- code_quality_explorer_{project_name}
- BrowserStack Role: Project Explorer
- Description: Users with this role can explore and view project details within the specified project.
- Example:
code_quality_explorer_PROJECTA
Configuration Options
Group Prefix Configuration
Global roles and project roles can be configured individually with SSO groups by enabling or disabling the “Group Prefix”.
- Enable Group Prefix: When enabled, the group prefix along with the project name will be mapped to SSO groups.
- Disable Group Prefix: When disabled, any group you specify will directly map to the corresponding role without needing the prefix.
Example Configuration
- If
enablegroupprefixis set tofalse:- Direct mapping of SSO groups to roles.
- If
enablegroupprefixis set totrue: